The term “social engineering” encompasses a broad spectrum of malicious activities. One of the oldest tricks in the book is phishing, which continues to be incredibly effective. In fact, 43 percent of cyberattacks in 2020 featured phishing or pre-texting, while 74 percent of US organizations experienced a successful phishing attack last year alone.
That means that phishing is one of the most dangerous threats to your organization’s cybersecurity. In addition, as more digital natives have come online, and greater awareness has been spread about phishing, bad actors have begun to diversify their phishing efforts beyond traditional email.
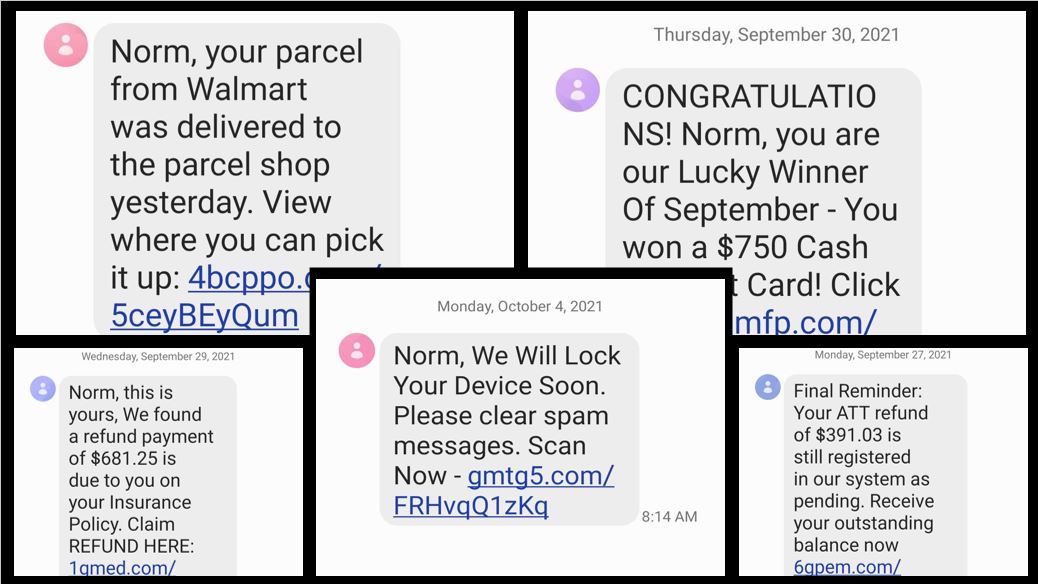
Beware of Smishing and Other Phishing Offshoots
Smishing attacks leverage malicious SMS text messages rather than email. Smashed messages usually contain links that launch a malicious site or download when tapped. Because it’s difficult to preview links that are in a text message, hackers may disguise the hyperlinked text as an email address, phone number, or other unassuming content a user might tap without hesitation. Smishing attackers often use social engineering to deceive their victims by impersonating a mobile service provider or other “official” source.
3 Ways to Block Smishing Attacks
Treat text messages the same way you would treat email, always think before you click:
- Verify the source. Many smishes will try to impersonate a service provider or other trusted source. This helps them trick you into believing their malicious content is actually safe.
- Don’t trust messages that attempt to get you to reveal any personal information, promise an unexpected item or reward (baiting), or threaten consequences if you don’t act immediately.
- Beware of similar tactics in platforms like What’s App, Facebook Messenger Instagram, etc.
Don’t fall for smishing texts. If you sense something unusual, reach out directly to the sender to confirm that the content is authentic and safe. If not, break-off communication immediately and flag the incident through the proper channels.
Vishing
Voice phishing — or vishing – is another alternative for bad actors looking to gain sensitive information from unsuspecting individuals. Similar to conventional phishing, vishing is typically executed by individuals posing as a legitimate organization — such as a healthcare provider or insurer. They then ask for sensitive information. Be wary of any communication that asks for personal information whether it be via email, phone or chat . This is especially true if the communication is unexpected. If anything seems suspicious, again, break-off the interaction immediately. Then contact the company directly to confirm the veracity of the communications. For more tips, see the infographic: 20 Ways to Block Mobile Attacks.
Another Dangerous Social Engineering Tactic – Pretexting
Whereas phishing attacks mainly use fear and urgency to their advantage, pretexting attacks rely on building a false sense of trust with the victim. This requires the attacker to build a credible story that leaves little room for doubt on the part of their target.
To mark the second week of Cybersecurity Awareness Month, we’re sharing a brief video all about pretexting. This social engineering tactic often involves scammers impersonating someone via email or phone to steal information. Join us live on Wednesday, October 13 for a lunch-and-learn demonstration showing how hackers can use pretexting to gain access to sensitive information over the phone using pretexting.
Stay tuned for more Cybersecurity Awareness Month activities!