And What You Should Do About It
An incident response plan is a set of instructions designed to help your organization identify, respond to, and recover from a cyber security incident. Hackers attack computers with Internet access every 39 seconds on average, and last year 1 in 5 organizations had an account compromised. Do you have an incident response plan ready for when a breach happens to your organization? If not, here are five reasons to start working on one immediately.
1. Lower Your Stress
Being the victim of a cyber incident guarantees that you are having a really bad day. I often joke that your first inclination may be to call your travel agent – so you can leave town before things get any worse. In all seriousness, you probably will not be thinking clearly when faced with the prospect of paying tens of thousands of dollars to a hacker, taking a hit to your reputation, or having your business grind to a halt.
Having an incident response plan and following previously documented steps takes a lot of the stress and guesswork out of your response. You also ensure that you are not missing any key steps in the process.
2. Mitigate Risk to Your Organization
According to IBM, organizations with incident response (IR) teams and testing spent about $2.46 million less on data breaches than those without preparations in place. The costs of a breach can be catastrophic to a small or midsized business – so keeping that number as low as possible may be your key to survival.
3. Recover More Quickly
Organizations that prepare for an incident in advance typically recover more quickly. Planning your response in advance can streamline the time it takes to stop lateral movement, shut off access, and ultimately eradicate the threat. In addition, the planning you have done beforehand to identify and protect critical systems and data will make it easier to recover via backup restore or other means.
4. Meet Compliance Requirements
The National Institute of Standards and Technology (NIST) 800-171 requirements outline incident response as one of the fourteen requirements. Likewise, organizations subject to Cybersecurity Maturity Model Certification (CMMC) level 2 or higher need to establish incident response capabilities. The Health Insurance Portability and Accountability Act (HIPAA) also requires a detailed plan for responding to cyber incidents.
5. Your Insurance Company Demands an Incident Response Plan
Earlier this year I spoke with insurance industry experts about the changing requirements around cyber insurance. Carriers have become more stringent about assessing risk before they are willing to provide coverage. Many now require an incident response plan as a mandatory item on their qualification checklist.
Getting Started With Your Incident Response Plan
Incident response planning starts with an understanding of your critical systems and data, and where your organization is vulnerable. Document the contact information for key resources who will be involved in responding to an attack, such as operations/IT, legal and communications. Remember, if your systems are down you may need to rely on alternate forms of communication such as secondary email addresses or phone numbers. Have a hard copy of the plan available in case it is not accessible online.
The incident response plan should also include processes for incident detection, containment, recovery, and post-incident activities. For example, how do you determine if data has been compromised? Who needs to sign off on a decision to contain the issue by shutting down critical systems? As I said before, following the process will go a long way toward removing emotions from the equation and making sure you follow steps that preserve forensic information without compromising business functionality. For more information, refer to NIST’s Computer Security Incident Handling Guide or check out this handy checklist from our partners at Datto.
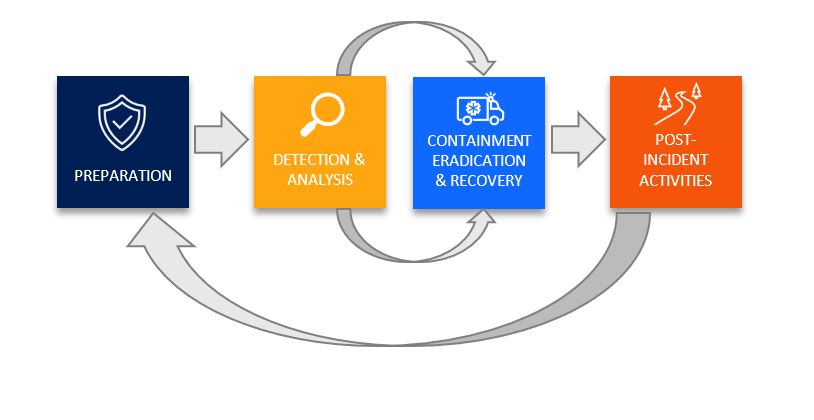
Once you have the plan ready, I recommend conducting a tabletop exercise or drill to go through it with the team. When that cyber security incident happens, you will be glad you took the time.
Feedback
If you have questions about this article, or if there is an IT topic you would like to know more about please email me your suggestions.
Referral$
If you know of a company that would be interested in the services of Invario, please email me the company name along with the phone number and email for the person we should contact.
That is all you have to do! Upon completion of the onboarding of a new customer, Invario will pay the equivalent of one month of Invario service to that customer. Recipients that cannot or do not wish to receive a referral payment may elect to have the referral fee donated to a charity of their choice or put into a company entertainment fund.

